BEIJING: China on Thursday released an investigation report revealing an “empire of hackers” of the Central Intelligence Agency (CIA) of the United States, one of the major intelligence agencies of the country’s federal government.
Over a long period, the CIA has been secretly orchestrating “peaceful evolution” and “color revolutions” around the world, continuously conducting espionage activities, said the joint report by China’s National Computer Virus Emergency Response Center and Beijing-based internet security company 360.
The report disclosed important details of the weapons the CIA used for cyberattacks and details of specific cybersecurity cases taking place in China and other countries.
The CIA has been involved in overthrowing or attempting to overthrow more than 50 legal governments of other countries, though it only admitted involvement in seven, causing turmoil in relevant countries, the report said.
Cyberspace hegemony
In 2020, the 360 company discovered an unknown cyberattack organization, which carried out a slew of cyberattacks toward China and other countries by utilizing cyber tools related to “Vault 7” – a series of documents that WikiLeaks began to publish in 2017 to expose the CIA’s activities and capabilities in electronic surveillance and cyber warfare.
Such cyberattacks can be traced back to the year 2011, and continue to this day. The targets of such espionage actions expand to fields such as countries’ key information infrastructure, the aerospace sector, scientific research institutes, the petroleum industry and tech companies, as well as government agencies.
The CIA has complicated inner workings. By the end of 2016, there were already over 5,000 hackers in the CIA’s hacking division – Center for Cyber Intelligence, producing more than a thousand hacking systems, Trojans, viruses and other “weaponized” malware, according to WikiLeaks.
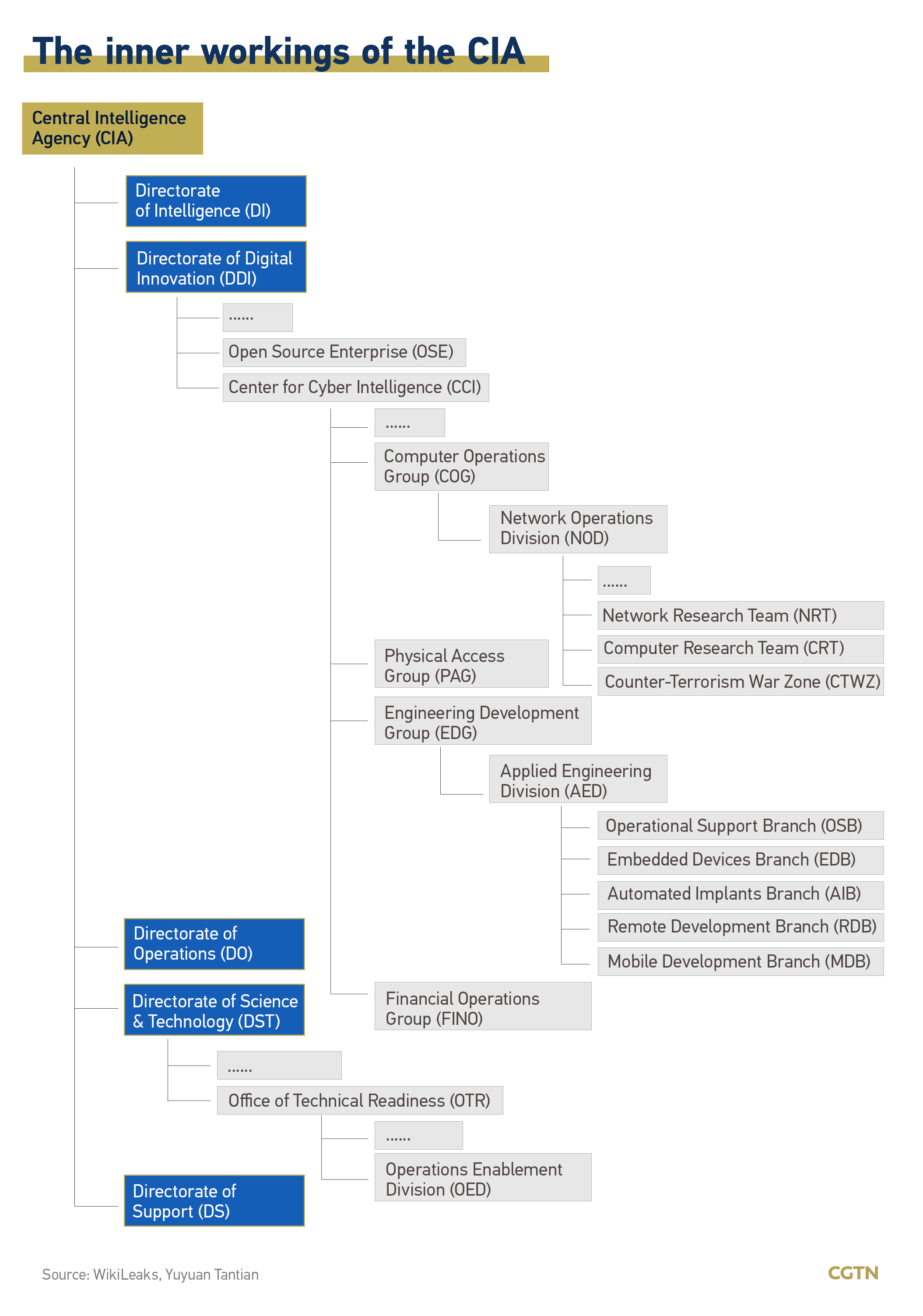
Yuyuan Tantian, a social media account affiliated with China Media Group, commented that the complexity of the organizational structure enables the CIA to tailor different tools to steal information.
For example, the agency divulged users’ secrets through smart TVs with their attack toolkit, Weeping Angel, developed by the Embedded Devices Branch. The toolkit can make TVs “pretend” to be switched off but in fact, they are still overhearing.
The report also noted that the Chinese technical team obtained a sample of an information interception tool that is exclusively used by the U.S. National Security Agency (NSA), indicating that the CIA and the NSA may jointly attack the same target, share attack weapons with each other, or provide technological or personnel assistance to each other.
Since 2015, the CIA massively has taken advantage of zero-day vulnerabilities in its global cyberattacks, setting up “zombie botnets” and “stepping stones” around the world to launch attacks on network servers, network terminals, exchangers and routers, as well as a huge amount of industrial control equipment, according to the report.
In the joint investigation, the team captured a plethora of malware such as Trojan programs and plug-ins related to the CIA. All the cyberattacking weapons were strictly standardized, processed and underwent professional software engineering management, and only the CIA abides by these standards and specifications to develop cyberattack weapons.
The investigation also found that the CIA’s cyberattacks cover all networks, which enables the agency to easily steal sensitive data of other countries at any time.























